Managed Services
MSSP
A Managed Security Service Provider (MSSP) provides outsourced monitoring and management of security devices and systems on and off premises. In addition, MSSPs provide local and remote response to security threats. Foresight offers the most advanced Managed Security Services available in the market today, combining consulting and professional services into a single managed solution. We provide security intelligence solutions that interfaces with multiple technologies, providing a proactive and holistic approach for defending your organization from sophisticated cyber threats. The implementation of our solutions is very easy and fast, increasing your security while saving you time and money. The foundation of the MSSP is built on:
- High-availability Security Operation Centers (SOC) with 24/7 services
- Security expertise as a service
- Managed security infrastructure
- Proven methods combining people, procedures and technology


SOC —Security Operations Center
A security operations center (SOC) is a dedicated site where enterprise information systems are monitored, assessed, and defended. SOC duties include:
- The SOC monitors and aggregates logs from the OT/IT infrastructure, applications and assets (on premise or cloud).
- The logs are stored on a dedicated SIEM to assess the data for threats and suspicious activity.
- The SOC also monitors applications to identify a possible cyber-attack or intrusion and determine if it is a real, malicious threat.
- The SOC is responsible for correlating events between the infrastructure application and other assets’ events.
- Playbooks
- Incidence response protocols
- Consistent review and updates
- Alert protocols
- Alerts Incident reports
- Incidents defended Incidents that require attention
- Defense and response teams comprised of group of experts that assess, document and respond to cyber incidents so that a network can recover quickly.
Cyber Security Intelligence
Cyber Security Intelligence is a service that shows you what you need to do in order to protect your organization. This service aggregates the intelligence feeds from the leading vendors to meet the latest cyber security challenges. Our partners include Symantec, Kaspersky, IBM and many more.
Expert as Service
Our best-in-class experts are on call for you, whenever and wherever you need them. Our security expertise covers a wide range of knowledge, therefore we can offer you hands-on guidance and advice relevant to your specific requirements and aid in developing your security operations. Let us help you improve staff efficiency and effectiveness. Our team of industry experts are up to date on the latest threats and current cyber security technologies. What’s more, in the event a major challenge arises that could affect your business, you are also covered by our best in class partners.
Cyber Security as a Service
We help you grow and run your internal security operations while reducing the need for long term infrastructure investments.
Remote
Backup
Secure File
Transfer
Mail Filtering
PRTG
Consulting Services
As technology continues to advance, so does the potential for increased cyber threats against the critical infrastructure of any organization. Unlike physical warfare, the distance between the attackers and the victims is irrelevant in cyber attacks, thus creating a bigger threat that proves even more difficult to identify, prevent and mitigate.
Governance, Risk Management & Compliance
Governance, Risk Management, and Compliance (GRC) are three facets that help assure that an organization meets its objectives.
Foresight has experts who have aided many organizations in achieving certified compliance with the newest regulations.
- Governance is the combination of processes established and executed by the directors (or the board of directors) that are reflected in the organization’s structure and how it is managed and led toward achieving goals.
- Risk management is predicting and managing risks that could hinder the organization to achieve its objectives.
- Compliance refers to adhering with the company’s policies, procedures, laws and regulations.
Foresight’s customized approach is based on industry standards and best practices. We produce the necessary documentation customized for the enterprise objectives.
Our Approach Leads to:
Better Business Performance Increased efficiency and profitability Effective decision making Less Risk
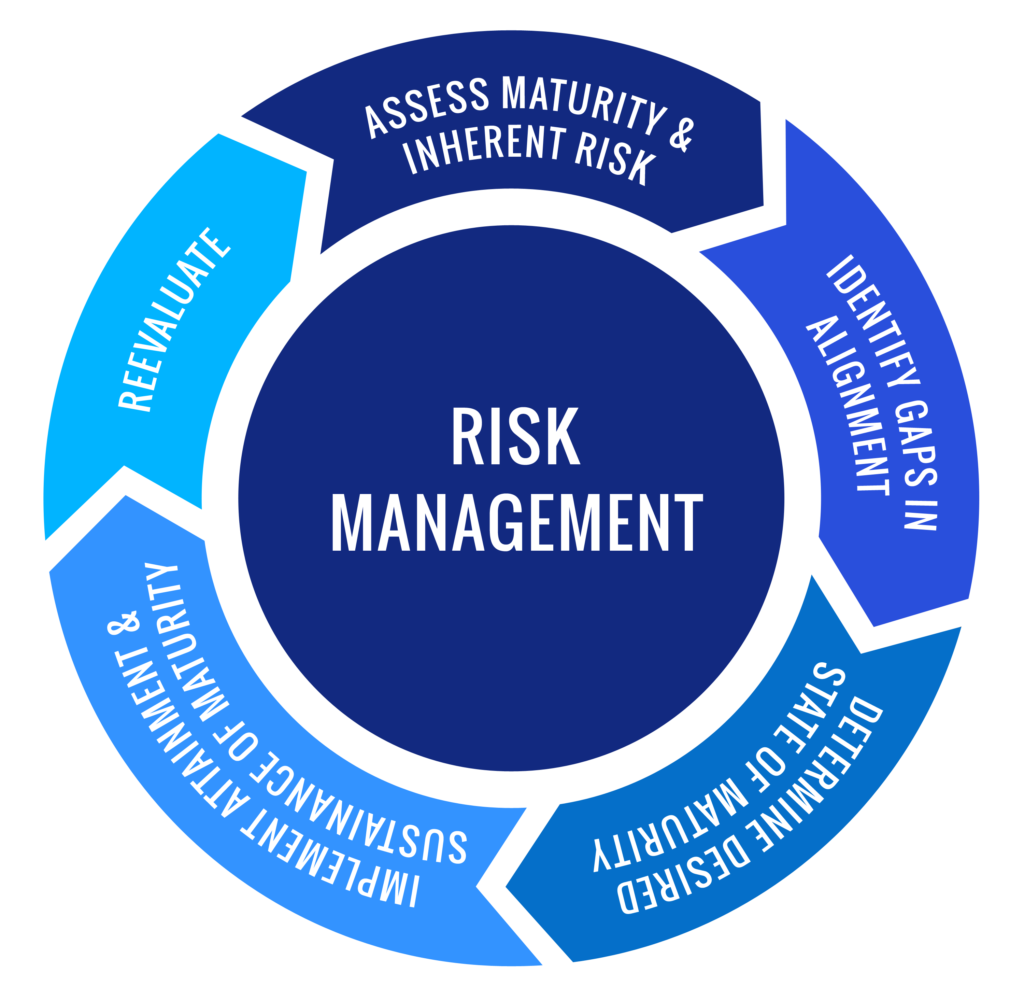
Risk Assessment
The probability of occurrences and the potential losses caused by the occurrence are not constant. These risks are constantly changing, causing the need for regular reassessment. The Foresight risk assessment methodology includes identifying areas within the business framework where the potential threats can interrupt the business flow. We deliver actionable recommendations to improve security, using industry best practices and the best technology available.
Security assessments:
- Identify, monitor, and analyze information related vulnerabilities effectively.
- Help you determine methods to manage or resolve data security risks.
- Spot potential data privacy and security compliance issues.
- Prioritize remediation steps into an effective plan based on your company’s specific goals, schedule, and budget.
Penetration Testing
Penetration testing and ethical hacking to identify information security weaknesses, preempt cyber threats and protect your critical digital assets. A penetration test, or pen test, is an attempt to evaluate the security of an IT infrastructure or application by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, service and application flaws, improper configurations, or risky end-user behavior. The penetration test may be within the framework known as:
White Box, which means the tester has received all information regarding the website, the application, and the network prior to initiating the test.
Black Box, which means that the tester acts as a hacker with little or no prior information prior to initiating the test.
SDLC
The Security Development Lifecycle (SDLC) is a software development process that helps developers build more secure software and address security compliance requirements while reducing development costs.

The SDLC process ensures that security assurance activities, such as architecture analysis, code review, and penetration testing, are an integral part of the development effort. The primary advantages of the SDLC approach are:
- Producing secure software, as security is a development concern
- Early detection of flaws in the system
- Cost reduction as a result of early detection and resolution of issues
- Overall reduction of intrinsic business risks for the organization
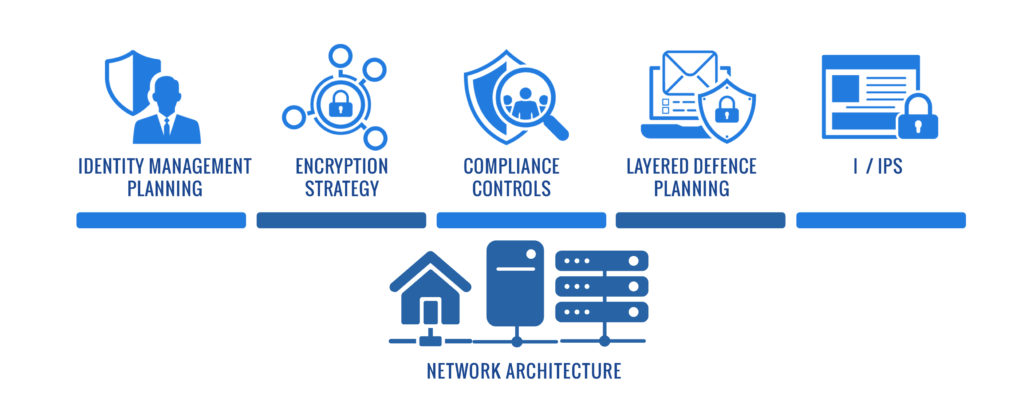
Professional Services
Your Security Partner
Foresight supports all of your organizational requirements including discovery, planning and design activities. We will identify your cyber security requirements and deliver the highest levels of protection for your existing infrastructure, budget, staff resources, and specific business requirements.
- Identity Access Management (IAM)
- Public Key infrastructure (PKI)
- Intrusion Prevention Systems (IPS)
- Security Information and Event Management (SIEM)
- Security Operations Centers (SOC)
- Endpoint Protection Platforms (EPP)
- Data Loss Prevention (DLP)
- Next Generation Firewall (NGFW)
- Secure Email Gateways (SEG)
- Secure Web Gateways (SWG)
- Network Access Control (NAC)
Foresight employs a team of enterprise security architects who understand enterprise security challenges and who are certified with the highest levels of accreditation from the leading security manufacturers in the world.
Foresight provides comprehensive management of your security projects, minimizing costs and freeing your staff to focus on higher value activities. We closely monitor tasks, people and milestones in the field to keep your project on schedule, and can provide 24/7 support to the project during critical phases.
Foresight sells, deploys and optimizes leading third party information security hardware and software, after assessing its relevance to the project at hand.
Foresight safeguards your business data from advanced mobile threats, implementing secure mobile access to business documents ensuring you can deploy and defend devices with confidence. We provide simple, unified management and policy enforcement to identify the data security, network security, advanced threat prevention, forensics and remote access VPN for complete endpoint protection.
Architecture
Cyber Security Architecture begins from the ground up by implementing industry proven best practice frameworks. Our experts offer the best evaluation assessments using the latest industry standards. Our architecture assessment includes design, planning, and implementation of the total security plan.